Activity 3.3: Analyze the Current State, Determine Adjustments, and Plan the Target State
This activity includes tasks that are very commonly related to architecture planning. Specifically, in this activity planners work with the collaborative planning team to assess the current business and data environment to form recommendations for how to change that environment to fulfill the strategic improvement opportunities. Then planners build from those recommendations to assess the current enabling application and infrastructure environment to form recommendations for how to change that environment to best enable the newly designed target business and data environment.Planners are working on a set of inter-related views of the environments that ultimately make up the target or future state. Strategic improvement opportunities need to be fulfilled. These strategic improvement opportunities can be fulfilled by changes in the business and data environment. The changes in the business and data environment generally must be supported or enabled by changes in the enabling applications and infrastructure environment.
One key part of this activity is the first task where planners review the vision materials from the previous activity and determine what type and levels of planning are required to form recommendations for how the vision can be achieved. All planning efforts are not the same and therefore it is critical that planners first think about what needs to be planned, how it needs to be planned, what information and materials are required as inputs and outputs of the planning, and then to set a project plan based on these conclusions. The end result will be a more nimble planning exercise where the materials produced from the analysis will be “just enough”, and “just in time” for making decisions. This is a hallmark of the modern planning environment where nimble planning is critical to achieve results.
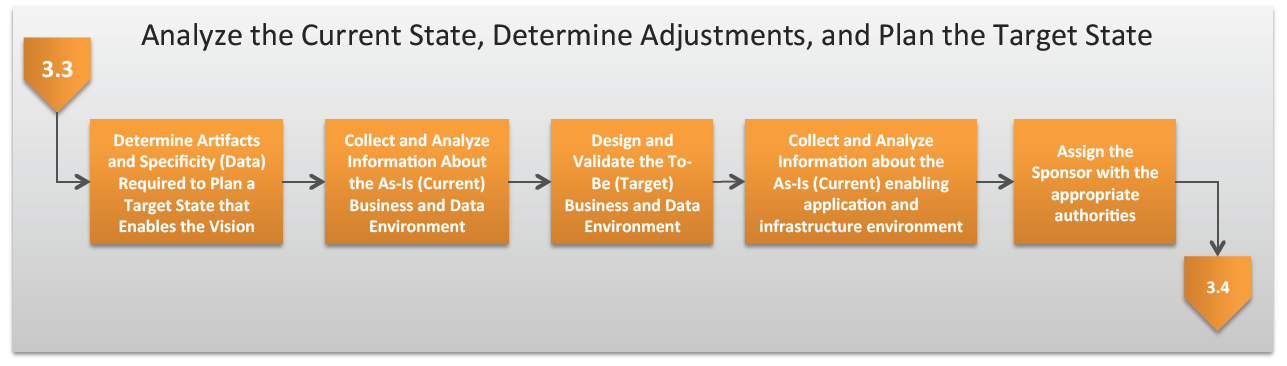
The following visual illustrates the tasks within this activity.
NOTE: This is the only activity within the Collaborative Planning Methodology (CPM) that includes both tasks and sub-tasks within the activity. The tasks involved with analyzing the current state, determining adjustments, and planning the target state are complex and require a deeper level of methodology. As a result, the CPM has been created to include sub-tasks in this section to provide more detail.
Tasks:
Determine Artifacts and Data (Appropriate Level of Specificity) Required to Plan a Target State that Enables the Vision
As previously stated, each planning effort is different and most require some form of tailoring of the approach based on the nature of the planning at hand. For instance, in some cases the planning might be more business focused while in other cases the planning might require a stronger technology focus. Furthermore, in some cases the planning might be at an international level of scope while in other cases the planning might be at an application level of scope.
In addition to the area of emphasis and level of scope, there could possibly be mandated compliance documentation or other requirements that influence the nature of the planning. Compliance requirements such as architecture plans, capital plans, security plans, records plans, Section 508 accessibility standards and others must also be considered in this task. Information that is required for each of these required plans must be assembled as part of the planning tasks and sub-tasks.
In this task, planners consider the area of emphasis and the level of scope for the prioritized needs and vision. Additionally the other compliance requirements are considered for applicability. Planners use this information to determine which artifacts and data are required to plan for the vision.
Sub-Tasks
3.311 Determine Level of Scope from the Common EA Approach
The document titled Common Approach to Federal Enterprise Architecture has documented the “levels of scope” and these levels of scope must be considered in this sub-task. There are eight levels of scope described in the Common Approach to Federal Enterprise Architecture:
International
National
Federal
Sector
Agency
Segment
System
Application
These levels of scope promote consistency in planning as different approaches and techniques can be used for the varying levels of scope. The level of scope of a particular planning effort can range from high-level views of one or more organization, to detailed views of a single segment, system, or application.
For the planning at hand, planners must assess the needs, strategic improvement opportunities, and especially scope to determine which of the levels of scope apply.
3.312 Determine Sub-Architecture Domain/Viewpoint Emphasis
Just as the Common Approach to Federal Enterprise Architecture describes the levels of scope, it also describes the concept of sub-architecture domains or what are called viewpoints in some planning communities.
Planning supports decision-making through the creation of recommendations and support materials across various aspects of the problem set at hand. There are six “domains” within and across which planning is conducted. When planning for a need, planners must consider recommendations within the following domains:
- Strategy
- Business Services
- Data and Information
- Enabling Applications
- Host Infrastructure
- Security Controls
Note: Several of the items in the list of domains are particularly IT focused. In many planning scenarios there may be an even broader list of non-IT domains depending on the nature of the needs being addressed.
For the planning at hand, planners must assess the needs and strategic improvement opportunities to determine which of the domains are relevant and which are of particular emphasis. As previously stated, some planning efforts will have strategic improvement opportunities that are more focused on business services while other planning efforts might have strategic improvement opportunities more focused on security controls. It is generally the case that most if not all sub-architecture domains are relevant, in varying degrees.
3.313 Determine Relevant Artifacts and Data (Appropriate Level of Specificity) required for each Sub Architecture Domain
Based on the conclusions drawn in the previous two sub-tasks, planners must determine which artifacts and data are appropriate for the planning at hand. Specifically, planners must focus on the artifacts and data that are relevant for the level of scope and specifically the level of detail required for the level of scope. Additionally, planners must focus on the domains or viewpoints that are of emphasis given the planning at hand.
Planners must review the artifacts types described in the Common Approach to Federal Enterprise Architecture (Documentation, p26) to determine which are appropriate for the planning at hand. Beyond just the artifacts, planners must focus on the data within the artifacts. Planners need to determine which data and to what specificity is required so that recommendations can be formed to meet the needs and vision.
3.314 Determine other information required for the integrated plan
There are a wide variety of compliance or required planning artifacts and reports depending on the nature of the planning and the organizations, countries, companies, or industries involved with the planning. In many instances, architecture plans, capital plans, security plans, records plans, specific types of transition plans, business cases, and other such documents are required for investments to be made. In such instances, it is important for planners to consider the needs and vision at hand and then determine which of the compliance or required planning artifacts will need to be produced during this planning process.
The intent is that after concluding with the Collaborative Planning Methodology, an integrated plan would exist and this integrated plan would include all the compliance or required planning artifacts.
3.315 Tailor the remaining steps of the methodology based on the artifacts identified in the previous steps
Planners now know the level of scope, the domains of emphasis, and the compliance or required planning artifacts associated with the needs, vision, and scope of the planning at hand. Based on this information, planners must leverage the list of remaining activities, tasks and sub-tasks in Step 3 to refine the project plan based on the specific needs of the planning at hand.
This tailoring approach allows for more nimble, cost effective planning. This tailoring approach also helps to reduce the risk of burnout within the collaborative planning team or loss of political will for an overly elaborate planning effort.
Planners must refine the project plan and then ensure that it is appropriately communicated to the collaborative planning team members, the sponsor, and governance.
Collect and Analyze Information about the As-Is (current) business and data environment
Planners have a project plan that is tailored to include the specific analysis activities that are required for the planning at hand. Based on this project plan, planners begin the process of collecting information about the current or as-is business and data environment. The business environment includes business functions, processes, rules, logic, and resources. The data environment includes the data that is being used within the business processes, the flow of data between and throughout processes, and the transformation of data into information as an output of the processes. When appropriate, the Business Reference Model and Data Reference Model described in A Common Approach to Federal EA may be used to assist in reviewing the current environment.
Planners need to gather this information about the business and data environment so that they can analyze the environment and determine what is driving the performance gaps and needs identified in Step 1. Planners are seeking to identify the constraints that are driving the existence of the strategic improvement opportunities.
Sub-Tasks
3.321 Collect information on the business functions and interdependencies relevant to the prioritized needs
In this sub-task, planners are determining the business functions that are relevant to the needs and vision so that those functions can be analyzed and recommendations can be formed in subsequent sub-tasks. Planners must first determine the business services that are being performed in the business environment. For instance, a business service could be payroll operations. Within the context of the needs and vision, there will be a few key business services that are important to the planning effort.
Once the key business services are identified, planners must map the needs and performance gaps to the services in order to determine a current level of service being provided. For instance, the payroll service might be lacking in advanced tax calculations and might take 50% too long to produce and process the payroll. This is the current level of service. This information is documented in the business services maturity matrix as the “level 0” or baseline level of maturity. In subsequent tasks planners will plan for incremental levels of business services maturity based on the level 0 maturity specifics.
Using the business services and the level 0 depiction in the maturity matrix, planners focus on the business processes that the organization must perform in order to deliver those business services. This analysis must begin with a high-level focus on the key business processes that deliver services, with the intent of identifying the critical chain of business processes that deliver value. The business services maturity matrix serves as a scoping tool to ensure that the planning effort maintains focus on the services that require attention, so the target vision, and goals and objectives can be achieved.
Each business service must be analyzed to determine the business area’s current chain of business processes that deliver each service. The chain of business processes will be diagramed using a value chain drawing. The value chain drawing is a high-level logical ordering of business processes that provides an overview of how value (i.e., product or service) is produced. The collaborative planning team must not default to an “analysis paralysis” mode; if the current value chain of business processes is determined to be ad-hoc, or if consensus cannot be determined, this may highlight a major finding and result in a recommendation for business process definition, optimization, or standardization. The planning scope may contain several value chains. However, to maintain a manageable scope, the focus must be on the few that most require attention.
Documenting the value chains is an important mechanism for determining the elements of the business environment associated with the strategic improvement opportunities. By focusing on a specific value chain, planners can perform additional business environment analysis on the areas of impact, based on the needs and vision.
Next it is important to define the business function model and associate it to the value chain. Planners associate the business processes in the value chain to their associated business function(s) in order to identify the magnitude of the business functions that will be affected by potential business process improvements. In the case of business processes that deliver enterprise services (e.g., geospatial, infrastructure), a full mapping is not necessary, although understanding the magnitude of functions affected is helpful in determining future implementation level impacts (e.g. scalability).
To define the business function model, business areas must be decomposed to define a hierarchy that includes functions and business processes. A business function is a logical set of business processes performed on a continual basis that has no specific beginning or end point. Functions are decomposed into business processes, which are a group of related business activities usually executed in a sequential fashion to achieve an intermediate or end-result product or service.
The business function model is created to show the critical business processes identified in the value chain analysis in the context of the business area functions. Existing reference models that catalog enterprise business functions may be used in structuring the functional hierarchy, but the business processes in the business function model must be consistent with the business processes defined in the value chain models. The intent of this documentation is to ensure that the business processes are affiliated with the business functions.
The information collection during this sub-task must also identify the organizations that perform the business processes and activities. Interactions across organizational boundaries in performing the business processes must be described so that ownership and accountability can be analyzed in subsequent sub-tasks. These interactions can be described using swim-lane diagramming techniques. In many instances, the analysis of organizational relationships to business processes and activities can yield critical insight into the current state environment.
Overall, it is important to document business processes and activities to a level that is meaningful for identifying requirements that will help achieve the strategic improvement opportunities. Extended process modeling efforts are not recommended unless clearly warranted based on the strategic improvement opportunities or the value chain analysis. In this case where additional projects may emerge, it may benefit the organization to return to an earlier step within the CPM to reprioritize the projects and their strategic value.
3.322 Identify and assess high-level information/data, dependencies, and information sources associated with the relevant business functions
Through the business process and activity analysis, planners have become more familiar with the business’s data environment. Although planners will document business modifications that can help achieve the strategic improvement opportunities, planners must re-use the business process and activity analysis to determine if there are information/data deficiencies that require adjustment to the current state.
For example, planners might have conducted business process analysis and determined that the business processes are sound but may also have noticed information-related deficiencies (e.g., insufficient data to make business decisions, redundant data entry between systems or manual routing of information that can be automated via information exchanges). In this case, planners may observe that there is an information collection and/or sharing deficiency whose resolution might lead to the achievement of a strategic improvement opportunity.
Planners must identify the high-level information requirements associated with the key business functions and processes identified in the previous sub-task. Planners need to determine where the data comes from, identify the major dependencies on the data besides the processes in focus for the planning, and define which information sources store the data.
Through the documentation of the business processes and information flows, planners must become familiar with the information requirements critical to the business. During this sub-task, planners must perform a qualitative analysis of the usefulness of key as-is information sources. The intent of this task is to document the sources of information in the current state before qualitatively assessing them along the key dimensions of accuracy, completeness, consistency, precision, timeliness, uniqueness, and validity. Part of the assessment of current data sources is the identification of existing security and privacy controls that are a part of the business’s workflow, data management practices, system designs, infrastructure management, and other protective measures.
Part of the development of target information services in later tasks is identifying target authoritative data sources (ADS) for key shared information. In this sub-task planners need to collect information on the myriad data sources including whether the same information exists in multiple sources and whether this information has become inconsistent because of differences in data management practices. This can be a root cause of business process and information delivery issues.
3.323 Analyze the business and data environment and determine the required strategic and operational business and data adjustments to fulfill the vision
Planners must analyze the gap between the current and required business environment in the context of the strategic improvement opportunities. In this sub-task, planners must determine which elements within the current state business and data environment must change to meet the desired strategic improvement opportunities. Planners must describe the needed changes to the business and data environments and whether any of these changes are currently addressed with planned initiatives or investments. The result of this sub-task is an articulation of the changes that must be made within the target business and data environment.
In order to determine which elements of the business environment to analyze, planners need to map the strategic improvement opportunities to the key business processes previously documented. In many cases, business processes are defined at a level too high to determine where deficiencies in performance or service delivery are occurring and may need to be decomposed to the activity level. Critical business processes must be defined at the activity level to derive high-level information requirements for the service. Although this methodology does not prescribe a standard modeling notation for this task, at a minimum, business processes must be modeled to depict information inputs, outputs, and value-added activities to perform the business process.
Using the mapping of business processes to strategic improvement opportunities, planners must determine the elements of the business environment that need to be adjusted to achieve the strategic improvement opportunities. For example, if the analysis of the current business processes reveals business process efficiency opportunities and those business processes are tied to strategic improvement opportunities, planners must determine if the business process efficiencies will help achieve those strategic improvement opportunities and therefore must be recommended. The intent of this analysis is not to attempt to re-engineer business processes by recommending numerous changes to the business environment, but to determine the key business processes and critical adjustments necessary to achieve the strategic improvement opportunities.
Planners must also do the research required to determine if business and IT initiatives are currently planned that would support the required changes in the business environment, and whether these initiatives would, when implemented, fully or partially, address the required adjustments.
Planners must document potential changes to the business environment that could help achieve the strategic improvement opportunities. Planners must use a formal template to document the limitations of the current state, desired characteristics of the target state, how the target state will help achieve the strategic improvement opportunities, and any known risk and cost considerations.
Once the business environment changes have been documented, it is important to also consider the data environment and changes that might be necessary. Just as with the business environment, planners must map the data environment to the strategic improvement opportunities to determine which elements of the data environment must be adjusted to achieve the strategic improvement opportunities. For example, if the analysis of the current business processes revealed information collection, storage, and sharing opportunities tied to strategic improvement opportunities, planners need to determine if the data environment opportunities will help achieve those strategic improvement opportunities and must therefore be recommended.
Part of the determination of adjustments to the data environment is the identification of existing security and privacy controls that will be a part of the business’s workflow, data management practices, system designs, infrastructure management, and other protective measures. The intent of this analysis is not to re-design the full data environment by making numerous information related recommendations, but to determine the key high-level adjustments necessary to achieve the strategic improvement opportunities.
Creation of new authoritative data sources (ADS) may be required to achieve identified strategic improvement opportunities. Planners must also do the research required to determine if there are business and IT initiatives currently planned that would address the changes in the data architecture and whether these initiatives would, when implemented, fully or partially address the required adjustments.
Planners must document potential changes to the data environment that could help achieve the strategic improvement opportunities. Planners must use a formal template to document the limitations of the current state, desired characteristics of the target state, how the target state will help achieve the strategic improvement opportunities, and any known risk and cost considerations.
3.33 Design and Validate the To-Be (Target) Business and Data Environment
During this task, planners must define the optimal target business and data environment to reflect each of the business and data changes identified in the prior sub-tasks. During this task, planners will define the target business and data environment by developing target versions of the current state business and data artifacts previously developed. Note that where possible, efforts should be made to maintain common domain semantics to model and describe the components in the business and data environment.
The scope of this analysis must focus only on critical business processes and data at an appropriate level of detail and granularity so as to:
- Identify the target state business processes and data
- Facilitate the derivation of the data environment from the business environment
- Maintain traceability between the business environment and data environment
In the end, the target business and data environment will be recommended for implementation in order to achieve the strategic improvement opportunities.
Sub-Tasks
3.331 Design target strategic and operational business environment, related performance, and organizational roles
Planners need to revisit the business services maturity matrix to design the maturity levels for the business services beyond level 0. In this sub-task, planners establish the target maturity levels that will contribute to achieving the vision while aligning to the desired performance metrics. With the establishment of these maturity levels, the collaborative planning team and sponsor can select target levels of business service maturity. This setting of maturity goals provides the information needed for planners to focus on specific business improvement targets.
For each target business service, planners must diagram the target chain of business processes in a value chain drawing describing the value that will be produced by the business processes. The target value chain might be identical to the current-state value chain because it is not uncommon for changes to be at the activity level rather than at the business process level. The intent of the target value chain analysis is to identify any differences in the business processes that are currently being provided, versus those that need to be provided in the target state. The value chain analysis will help determine where new business processes are required and where existing business processes may no longer be necessary.
Just as in the as-is analysis, the value chain must then be aligned to the target business function model. Planners must use the business function model to identify the critical business processes identified in the value chain analysis in the context of the business area functions. The business processes identified in the business function model must be consistent with the business processes identified in the value chain models. Additionally, it is necessary to ensure that the processes include built-in security and privacy controls, and compliance with Section 508 accessibility standards, that will provide proper levels of protection and accessibility that support effective business performance and which meet applicable laws, policies, directives, and guidance for the level of information criticality and sensitivity for the target business service.
For each key business process identified in the business function model and value chain models, it is necessary to define the target business processes and associated performance measures.
The business and data changes defined in previous sub-tasks are a major driver for the differences between the current and target state business process models. The business process models (e.g., IDEF0, BPMN) must be developed to describe the units of work, rules, guidance, enablers and performance measures for each key target business process.
Just as in the current state analysis, planners must understand the relationships between business processes and the organizations that perform or participate in those business processes. Using the business function model, value chain models, and business process models, planners must develop a target swim lane flow to describe a view of how organizational units interact in the context of the business processes that are delivering the services. Planners must make formal observations about accountability in the context of the organizations and their business processes.
3.332 Identify information/data, dependencies, and information sources associated with the target business environment
Using the target process models from the previous sub-task, planners must identify the information exchanged between key business processes along with the producers and consumers of that information and the mechanisms used to enable the exchange. Information access and exchange services must be summarized for information classes in a target information-sharing matrix.
Using the understanding of the key information flows developed in conjunction with the business process and activity analysis, planners must develop the target data model to provide a graphical representation of the data requirements and relationships. The data model will provide the structure and terminology for information and data in the target environment. The target data model must include subject areas, information classes, key entity types, and relationships.
The target data model must be used to update the data reference model (DRM) at the appropriate level. The target data model will be articulated to document data and its relationships to stewards and information sources. Planners must develop target data steward assignments by mapping each information class within the target data model to an organization that will be the data steward for that information class. The data steward is responsible for the creation, maintenance and quality of the data to support business activities in the target environment.
Based on the development of the target data steward assignments, planners must be able to communicate changes in stewardship and delivery of information. For instance, if two offices currently collect, store, and maintain the same data, and one office is designated as the steward, the other office could then become a customer of the steward office, rather than a second supplier of the same data.
In this sub-task planners must develop a matrix that documents how target business processes use the business information identified in the target data model (e.g., CRUD analysis). This matrix allows planners to map target business processes to core data entities to help identify candidate information services, including new authoritative data sources, and business processes that need to use these information services (preliminary requirements for orchestration). The matrix also helps identify producers and consumers of this information. At the end of this sub-task, the as-is key information sources must be updated with final recommendations concerning their designation as authoritative data sources.
The identification of information services is a key component to the target environment. This sub-task allows the planners to bridge the business and data domains by linking business processes and data. Through this analysis, planners must discover opportunities for re-use of information in the form of information sharing services. This analysis must also ensure that the information services include built-in security and privacy controls that will provide proper levels of protection that support effective business performance and which meet federal laws, policies, directives, and guidance for the level of information sensitivity. Planners must also look for information sharing service opportunities, within other parts of the enterprise and external to the enterprise.
3.333 Validate that the target business and data environment will fulfill the vision
Planners must review the outputs of the sub-tasks to ensure that the target business and data environments have adequately addressed the strategic improvement opportunities. During this sub-task, planners must review the business and data adjustment recommendations and the target business and data artifacts to ensure that there is full coverage of the strategic improvement opportunities.
Any strategic improvement opportunities that have not been addressed by the target business and data environments must be reviewed to ensure that the analysis is complete.
3.334 Package, present, and seek leadership approval of the business and data recommendations to achieve the vision
Planners must develop a package that describes the business and data environment and details recommendations for the collaborative planning team to review. This presentation must include a summary of how the business and data environment aligns with the needs, vision, goals and objectives, and performance metrics.
Planners must prepare a more detailed presentation that includes the business and data environments. The planners must conduct a detailed workshop review of the business and data environments with the collaborative planning team. The collaborative planning team must decide at this point whether to proceed into the next set of analysis activities or to refine the plans for the business and data environment further.
It is recommended that there be a formal sign-off of the materials by the sponsor and governance.
3.335 Draft applicable portions of architecture, capital planning, security, records, budget, human capital, and performance compliance documents
In many organizations there are significant compliance or required documents associated with planning. At the start of this task planners determined which of these compliance or required items are applicable to the planning at hand.
Based on this assessment, planners should have been gathering the required data for the compliance documents throughout the sub-tasks. It is in this sub-task that planners leverage the information to begin creating the compliance documents.
Initial drafts of the relevant architecture, capital planning, security, records, budget, human capital, and performance compliance documents must be developed based on the guidance associated with those compliance documents. Note that at this stage of the CPM it is likely that more information will be needed to complete these compliance documents. As such, these compliance documents will be revisited in a later sub-task.
3.34 Collect and Analyze Information about the As-Is (Current) enabling application and infrastructure environment
This activity builds upon the analysis of the business and data environment performed in previous sub-tasks and is within the scope identified in Step 1. The focus of this task is to collect and analyze information pertaining to the as-is use of applications and infrastructure and how well those applications and infrastructure support the desired performance as well as how well they enable the business and data environment. Note that where possible, efforts should be made to maintain common domain semantics to model and describe the components in the enabling application and infrastructure environment. When appropriate, the Application Reference Model and Infrastructure Reference Model described in A Common Approach to Federal EA may be used to assist in this standardization.
This task includes assessing the applications and infrastructure across several dimensions, including business, data and technology alignment; service management; and maturity. This task also includes a high-level assessment of existing application interfaces and the data that is exchanged between those applications.
By performing an analysis of existing applications and infrastructure against the desired performance as well as the extent to which the business and data environment is enabled, planners must be able to answer key questions related to the application and infrastructure environment including:
- How well are the applications and infrastructure delivering business value in relation to the costs associated with operating and maintaining them?
- What is the relationship between the existing applications, infrastructure, and technologies (i.e., as-is solution architecture)?
- What existing applications are associated with authoritative data sources?
- How efficient is my infrastructure?
Sub-Tasks
3.341 Collect and assess information on the enabling applications and infrastructure associated with the business and data environment
During this task, planners gather information that will be useful to conducting an analysis on how well the current applications and infrastructure support target business services. Information being gathered may include the applications currently in use, infrastructure currently in use, any known security issues or risks, and stakeholder feedback with regard to overall application performance and alignment to business needs. Performance information may also be derived from existing program performance assessments.
Information gathering can be performed using a variety of methods, including querying an existing repository of information and conducting interviews with key stakeholders (e.g., business owners, application owners) to understand the applications and infrastructure within a business service and to identify existing data sources. The information collected must be at a sufficient level of detail to assess the data fit, business fit, technology fit, service management, and maturity level of the application or infrastructure and must include the total cost to provide, deliver, support, and manage data, applications, and infrastructure in the portfolio.
The cost information gathered during this task must be leveraged to create required outputs for capital planning and investment control such as the cost-benefit analysis and return-on-investment analysis that will be utilized in the development of business cases. For example, if redundant applications and infrastructure are identified for decommissioning in subsequent activities, it will be helpful to have determined an estimated cost for the current environment.
The as-is solution architecture serves as a baseline for determining the required adjustments to the environment in order to align the strategic, business, and data improvements defined in previous tasks. Planners must develop an understanding of the current applications and infrastructure environment so subsequent analysis of the target applications and infrastructure architecture can be performed.
The as-is applications and infrastructure interface diagram(s) must be constructed to illustrate how the business functionality identified in the business model is associated with existing applications and infrastructure. This model shows the existing applications and infrastructure in the as-is state and identifies the relationships (e.g., data exchange packages) between them, but it may also include an overlay to show the boundaries of key business functions and external interfaces (e.g., organizational). The data depicted in the as-is applications and infrastructure interface diagram(s) must align with portions of the data model, and the applications and infrastructure depicted must be enablers of the business processes and activities already analyzed.
Unlike the description of the target solution architecture, the description of the as-is model must include only the as-is applications and infrastructure interface diagram(s) in order to limit the analysis of the as-is solution architecture to what is necessary to provide an adequate baseline. The subsequent development of the target solution architecture will include other artifacts.
3.342 Identify applicable technology, service, and information standards
High-level technology, service, and information standards for the target enabling applications and infrastructure environment must be specified with the goal of maintaining alignment with the desired performance as well as the enabling business and data requirements.
This sub-task begins with a review of the target business and data environments previously defined, along with the target maturity level for services. The purpose of this review is to ensure that the specification of high-level technology, service, and information standards are aligned with the overall strategic improvement opportunities defined in previous planning activities.
For each major business function, the required services and associated standards must be identified. This includes:
- Identifying service interface needs
- Defining high-level requirements related to security controls
- Identifying information services required to support authoritative data sources
- Identifying the maturity level for the underlying capabilities needed to deliver the service
- Identifying technology standards or ensuring that existing technology standards are being adopted appropriately
3.343 Analyze the enabling applications and infrastructure environment and determine required adjustments to enabling applications and infrastructure to enable the target business and data environment
An assessment of the value and performance of as-is enabling applications and infrastructure within the defined scope of the planning is performed to determine where adjustments to the application and infrastructure environment must be investigated. This assessment is critical to ensure alignment to the strategic, business, and data requirements depicted in previous sub-tasks.
An overall assessment is performed for each as-is application and infrastructure component to determine how well the application or infrastructure component supports the vision previously developed. This assessment must also include an identification of the degree of functional overlap with other applications or infrastructure components and the extent to which the application or infrastructure components are associated with re-engineered or streamlined business processes (e.g., automated workflow).
The business value assessment must also take into consideration the overall efficiency of applicable investments (e.g., return on investment) relative to available alternatives to these investments in similar applications and infrastructure or to other enterprise services.
Results of the as-is applications and infrastructure analysis are compiled and evaluated using the as-is system and services scorecard, which produces a comprehensive scoring of the cost, fit, and value of as-is systems. The analysis results must be evaluated to answer key questions relative to the needs of the target application and infrastructure environment, including:
- What existing investments are included in this portfolio?
- What are the applications and infrastructure in the portfolio and how are they deployed?
- How well are the applications and infrastructure able to deliver business value for the costs associated with operating and maintaining them?
- What risks are associated with existing applications and infrastructure?
- What applications or infrastructure must be considered for the target state?
- What security and privacy continuous monitoring activities must be considered for the target state?
- How efficient is my infrastructure?
3.35 Design and Validate the To-Be (Target) Enabling Applications, Services and Infrastructure Environment
In this task planners design and validate the to-be or target enabling applications and infrastructure environment to best enable the business and information environment. A complete depiction of the target state must include a depiction of the target applications and infrastructure that is consistent with the existing enterprise architecture and compliant with Section 508 accessibility standards. In addition to applications and infrastructure, planners need to define the technical and service standards used to automate and improve business functions within the scope of the planning. The scope of the target depiction in this task includes data sources, applications, and the interfaces between them. The target depiction in this task must also describe the boundaries defined by interfaces with external customers, applications, services, and organizations.
As a general rule, the specification of technical components must, in principle, be vendor-agnostic within the outputs of this task. As such, the depictions of applications and infrastructure must not be specific or unique to a particular solution or vendor. The key exceptions to this rule are where existing as-is systems, standard commercial off the shelf (COTS) solutions, and solutions purchased through enterprise license agreements (ELAs) are to be included as part of the target state. This integrated view will greatly improve the hand-off to implementers by providing a means for linking applications to data and their supporting technology components.
Sub-Tasks
3.351 Determine required target enabling applications and infrastructure to enable the target business and data environment
The result of completing this task is the selection of applications and infrastructure to be included in the target state, based on the desired performance as well as the enabling business and data environments. Planners must review the results of the business value analysis, combined with the specification of technology, service, and information standards in prior sub-tasks, to identify target applications that provide the necessary capabilities to support the target business and data environments. This analysis must also take into account how the existing applications and infrastructure are performing in terms of business value and cost. High business-value applications in the current state could be good candidates for the target state environment.
Selecting target-state applications may mean carrying forward an existing application to the target state, consolidation of multiple applications to reduce the total number of applications supporting a business function, and/or identification of a new high-level application requirement associated with automation of business processes.
As the development of the target application and infrastructure environment is tightly coupled with the business and data environment, this sub-task may become highly iterative as changes to the business and data environment are identified.
3.352 Identify the relationships and data exchange requirements between the target enabling applications
In this sub-task planners need to define the relationships between applications and infrastructure within the context of the overall boundaries. Planners must construct the target applications and infrastructure interface diagram(s) to illustrate how the business functionality identified in the business model is associated with target application and infrastructure components, including the definition of data exchange packages that need to exist between applications.
The target applications and infrastructure diagram(s) must show the applications and infrastructure in the target state and identify the data exchange relationships between them. This diagram may include an overlay to show the boundaries of key business functions and external interfaces. The diagram(s) must also depict the authoritative sources of record for data and how that data gets deployed in the applications view.
The planners could capture target application services in an application service component model (ASCM), an analytical technique that may be applied to business and enterprise application services to describe application service components and the mechanisms for providing application services to customers. This model, which provides a framework and vocabulary for guiding discussions between application service providers and consumers, is meant to be a catalyst for true cross-organization collaboration. Along with development of the ASCM, the technology model (TM) can be developed to show the technology components that support the business service delivery for each application service component defined in the ASCM.
3.353 Package, present, and seek leadership approval of the enabling applications and infrastructure recommendations to enable the target business and data environment
Planners must develop a package that summarizes the as-is and the to-be application and infrastructure environment and provide an overview of the benefits of this environment on desired performance and the vision. This must include the relevant artifacts describing the target application and infrastructure environment and how they enable the performance, business, and data environments.
Planners must conduct a detailed workshop review of these outputs for the collaborative planning team. The review must also include key IT personnel.
It is recommended that there be a formal sign-off of the materials by the sponsor and governance.
3.354 Update applicable portions of architecture, capital planning, security, records, budget, human capital, and performance compliance documents
In many organizations there are significant compliance or required documents associated with planning. At the start of this task planners determined which of these compliance or required items are applicable to the planning at hand.
Based on this assessment, planners should have been gathering the required data for the compliance documents throughout the sub-tasks. It is in this sub-task that planners leverage the information to update and potentially finalize the creation of the compliance documents.
Updated or potentially final drafts of the relevant architecture, capital planning, security, records, budget, human capital, and performance compliance documents must be developed based on the guidance associated with those compliance documents. Note that at this stage of the CPM, most of the information required for these documents must be gathered and ready to be used in the documents.
Activity Outputs:
| Output | Core | FEA Layers |
|---|---|---|
| Common / Mission Services Target Maturity Levels | Y | B |
| As-Is Business Value Chain | Y | B |
| As-Is Business Function Model | Y | B |
| As-Is Key Business Process Model | N | B |
| As-Is Business Process Swim Lane Diagram | N | B |
| As-Is Key Information Sources and Qualitative Assessment | Y | D |
| As-Is Business Data Mapped to Key Business Processes (CRUD) | N | B, D |
| As-Is Data Model Y D As-Is Data Steward Assignments | Y | D |
| Business and Data Architecture Adjustment Profiles | N | B, D |
| Target Business Value Chain Diagram | Y | B |
| Target Business Function Model | Y | B |
| Target Key Business Process Model | N | B |
| Target Business Process Swim Lane Diagrams | N | B |
| Target Business Data Mapped to Key Business Processes (CRUD) | N | B, D |
| Target Data Model Y D Target Data Steward Assignments | Y | D |
| Business and Data Environment Presentation | N | B, D |
| Draft Architecture, Capital Planning, Security, Records, Budget, Human Capital, Section 508 Accessibility and Performance Compliance Documents Y n/a As-Is Enabling Application and Infrastructure Architecture | Y | A, I |
| As-Is Application Scoring | N | A,I |
| Enabling Application and Infrastructure Architecture Adjustment Profiles | N | A, I |
| Target Enabling Application and Infrastructure Architecture | Y | A,I |
| Target Information Flow Diagram | Y | A, D |
| Target Information Sharing Matrix | N | A, D |
| Enabling Applications and Infrastructure Presentation | N | n/a |
| Updated Architecture, Capital Planning, Security, Records, Budget, Human Capital, Section 508 Accessibility and Performance Compliance Documents | Y | n/a |
Key to FEA Layers: S = Strategy, B = Business, D = Data, A = Application, I = Infrastructure, SP = Security