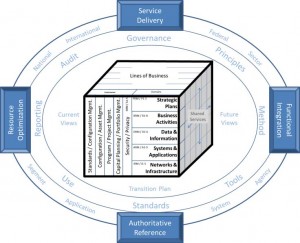
EA supports planning and decision-making through documentation and information that provides an abstracted view of an enterprise at various levels of scope and detail.
- Strategic
- Business Services
- Data and Information
- Enabling Applications
- Host Infrastructure
- Security
These six sub-architecture domains delineate the types of analysis and modeling that are necessary to meet stakeholder requirements.
Based on EA best practices, the Common Approach to Federal EA lists one required core documentation artifact for each of the six sub-architecture views. This serves to promote consistent views within and between architecture as well as promoting interoperability within and between government organizations.
Required Core Artifacts List:
Strategy – Concept Overview Diagram
Business – High-Level Process Diagram
Data – High-Level Logical Data Model
Applications – Application Interface Diagram
Infrastructure – High-Level Network Diagram
Security – Control List
There are also several dozen elective artifacts identified in the Common Approach to Federal EA to support additional analysis if that is needed. The type and depth of documentation should be guided by the need for detail and answers to questions about requirements, applicable standards, timeframes, and available resources.
The high-level graphical/textual description of the operational concept
S-2: Strategic Plan
A description of the organization’s vision, strategic objectives, a prioritization of the desired outcomes from achieving those objectives, the measurements that will demonstrate achievement, and the resources to be used to achieve them
S-3: Concept of Operations Scenarios
Organizes Business Process Sequences into scenarios
S-4: SWOT Analysis
Presents the Strengths, Weaknesses/Limitations, Opportunities, and Threats involved in a project or in a business venture including risks and impacts
S-5: Performance Measures Scorecard
A strategic performance management tool that can be used by managers keep track of the Performance Metrics associated with the execution of activities by the staff within their control and to identify the Performance Gaps and consequences arising from these gaps
Presents the hierarchical structure of organizational activities and activities performed by organizational performers to consume and produce resources
B-2: Business Operating Plan
Describes, from a timeline perspective, the changes to the Business Service Catalog, Organizational Chart, and Business Process Model to transition from the current state to the objective state
B-3: Business Service Catalog
Presents the business services, taken from the BRM, that are provided within the scope of the architecture and may also indicate business services that are consumed or used internally within the architecture
B-4: Organization Chart
Presents the composition and relationships among organizational performers
B-5: Use Case Narrative and Diagram
Describes a set of possible sequences of interactions between systems and users in a particular environment and related to a particular goal
B-6: Business Case / Alternatives Analysis
A summary of the planning, budgeting, acquisition, and management of federal capital assets sufficient to determine if investment funding should be recommended or continued
Presents data requirements that reify the information concepts identified by corresponding Conceptual Information models
D-2: Knowledge Management Plan
Provides a detailed description of how knowledge, information, and data are shared across the enterprise between systems, applications, knowledge warehouses, and databases
D-3: Data Quality Plan
A systematic approach to data quality assurance
D-4: Data Flow Diagram
The functions (activities) performed by systems or services, their hierarchical structure, and their resource flows
D-5: Physical Data Model
Presents data-elements and data-structures that reify the data requirements specified by corresponding logical data models
D-6: CRUD Matrix
Presents resources that are consumed and produced by activities performed by organizational performers
D-7: State-Transition Diagram
The states systems transition to in response to events
D-8: Event Sequence Diagram
A sequence of triggering events associated with resource flows and systems
D-9: Data Dictionary
A centralized repository of information about data such as name, type, range of values, source, and authorization for access for each data element in the organization’s files and databases
D-10: Object Library
A collection of computer programs in the form of relocatable instructions, which reside on, and may be read from, a mass storage device
Application Interface Diagram (core)
The identification of application resource flows and their composition
A-2
Application Communication Diagram
The means by which resource flows between applications occur
A-3
Application Interface Matrix
The interface relationships among systems
A-4
Application Data Exchange Matrix
The details of resource flows among systems; the activities performed; the resources exchanged; and the attributes (rules and measures) associated with these exchanges
A-5
Application Service Matrix
Interface relationships between services and applications
A-6
Application Performance Matrix
The measures (metrics) of applications
A-7
System / Application Evolution Diagram
The planned incremental steps toward migrating a suite of systems and/or applications to a more efficient suite, or toward evolving a current system or application to a future implementation
A-8
Enterprise Service Bus Diagram
Describes the interaction and communication between mutually interacting software applications in service-oriented architecture (SOA)
A-9
Application Maintenance Procedure
Describes how to modify software to provide error corrections, enhancements of capabilities, deletion of obsolete capabilities, and optimization
A-10
Application Inventory
A registry of applications and services, the system functions or service activities they perform, and, optionally, prioritized or ranked.
A-11
Software License Inventory
A list of Commercial-off-the-Shelf (COTS) and open source software assets with details about each (installation date, original cost, condition and such).
Network Diagram (core)
Describes the means by which resource flows between systems occur
I-2
Hosting Concept of Operations
Presents the high level functional architecture, organization, roles, responsibilities, processes, metrics and strategic plan for hosting and use of hosting services
I-3
Technical Standards Profile
Collects the various systems standards rules that implement and sometimes constrain the choices that can be made in the design and implementation of an architecture
I-4
Technology Forecast
The emerging technologies, software/hardware products, and skills that are expected to be available in a given set of time frames and that will affect future infrastructure development
I-5
Cable Plant Diagram
Diagrams the wires and connectors used to tie a network together
I-6
Wireless Connectivity Diagram
Diagrams a communications network that provides connectivity to wireless devices
I-7
Rack Elevation Diagrams (front and back)
Two-dimensional elevations, drawn to scale and showing everything that needs to be placed in a certain area, that describe the organization of specific equipment on a rack
I-8
Data Center / Server Room Diagram
Diagrams the layout and contents of a data center or server room
I-9
Wiring Closet Diagram
Diagrams the layout and contents of a wiring closet
I-10
Point of Presence Diagram
I-11
Asset Inventory
A list of assets with details about each (installation date, original cost, condition and such).
I-12
Facility Blueprints
Technical drawings of the facility
SP-1
Security Controls Catalog (core)
Describes the total set of security controls from which the developer may choose those that are applicable for the effort
SP-2
Security and Privacy Plan
A description of the enterprise security and privacy programs, policies and procedures for the agency
SP-3
Security Authorization Documentation
Compilation of security documents relevant to each system such as: System Security Plan, Risk Analysis, Security Requirements Traceability Matrix, System Security Authorization Agreement, Authority to Operate, etc.
SP-4
Continuous Monitoring Plan
Describes the organization’s process of monitoring and analyzing the security controls and reporting on their effectiveness
SP-5
Disaster Recovery Plan
A plan that describes all aspects of recovery from an incident that temporarily disables the operational capabilities of the enterprise, but does not entail re-location
SP-6
Continuity of Operations Plan
A plan that describes all aspects of recovery from an incident that temporarily disables the operational capabilities of the enterprise, and does require re-location