Local Area Network (LAN) Artifacts
-
Standards and Guidelines
Brief Overview
Our LAN network is set up as follows:
- All connections are made with fiber optics. This is the standard for all the servers and to the switches and router and bridges.
- The layouts shown in the TOPOLOGY link are the type dependent on floors and building.
- The switches/routers are from Cisco systems. They can support the network activity of 20 Meg connections for workstations and the 100 Meg for the database servers.
- For the connection between buildings, we are using fiber optics again.
- Connecting to the outside network, we use a T1 line.
- We have both a software and hardware firewall to protect our internal network. The firewall is made by Cisco and there are a number of different software firewalls.
- The number of workstations and the number of floors per building will determine the number of routers needed.
The main office in Houston is where the data center/main server room is located. All the other workstations and servers are backed up to this location, using the netback tool.
Topology
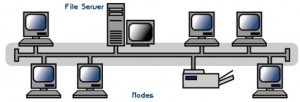
Linear bus topology consists of a main run of cable with a terminator at each end (See Figure 1). All network nodes (file server, workstations, and peripherals) are connected to the linear cable. Ethernet and LocalTalk networks use a linear bus topology.
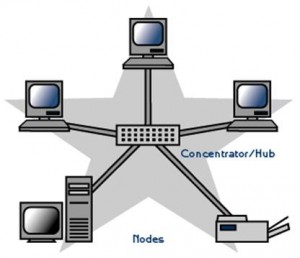
A star topology is designed with each node (file server, workstations, and peripherals) connected directly to a central network hub or concentrator (See Figure 2).
Data on a star network passes through the hub or concentrator before continuing to its destination. The hub or concentrator manages and controls all functions of the network. It also acts as a repeater for the data flow. This configuration is common with twisted pair cable; however, it can also be used with coaxial cable or fiber optic cable.
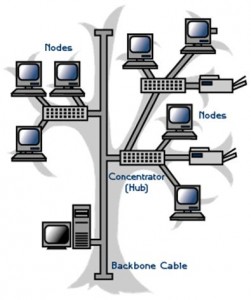 A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable (See Figure 3). Tree topologies allow for the expansion of an existing network and enable schools to configure a network to meet their needs.
A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable (See Figure 3). Tree topologies allow for the expansion of an existing network and enable schools to configure a network to meet their needs.
 Peer-to-peer network operating systems allow users to share resources and files located on their computers and to access shared resources found on other computers. However, they do not have a file server or a centralized management source (See Figure 4). In a peer-to-peer network, all computers are considered equal; they all have the same abilities to use the resources available on the network. Peer-to-peer networks are designed primarily for small to medium local area networks. AppleShare and Windows for Workgroups are examples of programs that can function as peer-to-peer network operating systems.
Peer-to-peer network operating systems allow users to share resources and files located on their computers and to access shared resources found on other computers. However, they do not have a file server or a centralized management source (See Figure 4). In a peer-to-peer network, all computers are considered equal; they all have the same abilities to use the resources available on the network. Peer-to-peer networks are designed primarily for small to medium local area networks. AppleShare and Windows for Workgroups are examples of programs that can function as peer-to-peer network operating systems.
Future View
DMC Future View for the Wireless LAN Network:
Wireless, if wisely applied, offers extraordinary opportunities. The opportunities are only going to be realized by building the communications infrastructure to support the wireless LANs.
Bluetooth started out as a consortium and still remains an active consortium of companies with an interest in cable replacement technologies with a range of 30 feet. The small chipset size and very low cost ($3-$20 chipset cost) is the design criteria. The Bluetooth consortium specification used 2.4GHz fast frequency hoping in its deployment IEEE 802.11b standard, an 11Mbps Direct Sequence version, and is the most popular.
Security & Recommendations
The goal of any comprehensive WLAN security plan should be to protect the network from attack from within, as well as from the outside. Maintaining a secure wireless network and associated devices requires significant effort, resources, and vigilance and involves the following steps:
- Managed Security Services to offer comprehensive solutions for real-time security management including system monitoring, emergency response and 24/7 guaranteed protection
- Stop the unwanted material DMC employees receive in e-mail. Managed Security Services for e-mail security can provide a variety of solutions to enhance existing security posture that will help to prevent viruses, spam and control unwanted content in e-mail.
- Managed Security Services for Web security to protect DMS from Internet threats with 24/7 scanning that helps stop viruses and spy ware before they can compromise the network. Simple to deploy and easy to manage, with robust antivirus, anti spy ware and URL-filtering technologies
- Prepare ahead for information security breaches or stop attacks in progress with Emergency Response Services from Internet Security Systems
- Work with expert security consultants to help bring DMS systems into compliance with industry and government regulations for information security.
- Maintaining a full understanding of the topology of the wireless network
- Performing periodic security testing and assessment of the wireless network
- Applying patches and security enhancements
- Creating backups of data frequently
- Labeling and keeping inventories of the fielded wireless and handheld devices
- Labeling and keeping inventories of the fielded wireless and handheld devices
- Performing ongoing, randomly timed security audits to monitor and track wireless and handheld devices
Risks and Mitigation
Because it is much more difficult to address security once deployment and implementation have occurred, security should be considered from the initial planning stage.
The risks related to the use of wireless technologies are considerable. Many current communications protocols and commercial products provide inadequate protection and thus present unacceptable risks to agency operations. DMC must actively address such risks to protect their ability to support essential operations, before deployment of wireless technologies.
Wireless LANs Access points being considered
Each access point typically supports up to 255 client computers. By connecting access points to each other, local networks having thousands of access points can be created. Client computers may move or “roam” between each of these access points as needed:
- Houston, TX – 20 access points,
- Los Angeles, CA – 10 access points,
- Jacksonville, Florida – 10 access points,
- Phoenix, AZ – TBD
Benefits:
WLANs offer four primary benefits:
- User Mobility—Users can access files, network resources, and the Internet without having to physically connect to the network with wires. Users can be mobile yet retain high-speed, real-time access to the enterprise LAN.
- Rapid Installation—The time required for installation is reduced because network connections can be made without moving or adding wires, or pulling them through walls or ceilings, or making modifications to the infrastructure cable plant. For example, WLANs are often cited as making LAN installations possible in buildings that are subject to historic preservation rules.
- Flexibility—Enterprises can also enjoy the flexibility of installing and taking down WLANs in locations as necessary. Users can quickly install a small WLAN for temporary needs such as a conference, trade show, or standards meeting.
- Scalability—WLAN network topologies can easily be configured to meet specific application and installation needs and to scale to very large enterprise networks that enable roaming over a broad area.
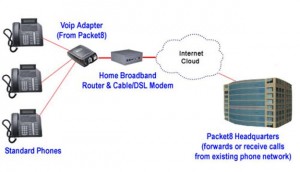
VOIPDMC will use VOIP to prevent network phone drops. Voice over IP (VoIP) is the transfer of voice conversations as data over an Internet Protocol (IP) based network. (See Figure 5). Advantages to this new technology are that VoIP service allows phone numbers to no longer have any direct relationship to where in the world someone is located. A phone can work anywhere in the world where there is a broadband internet connection, and any area code can be used. For example, a military family living in Germany could have a Chicago phone number and could make and receive calls to and from the US.