 EA3 artifact SP-6: Continuity of Operations Plan
EA3 artifact SP-6: Continuity of Operations Plan
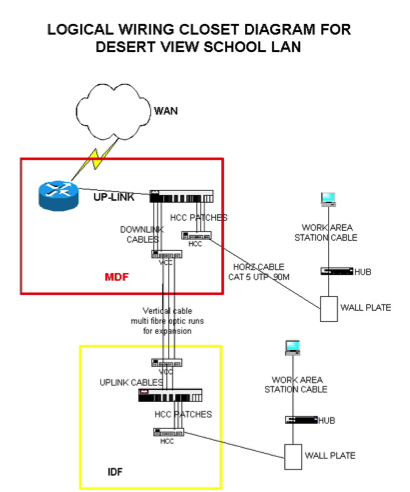
The Continuity of Operations Plan (COOP) uses a standard format for describing where all or part of the enterprise will relocate to if the normal operating location cannot be occupied for an extended period (more than a few days) due to a natural or man-made event.
The activation of the COOP relocation site may have to be accomplished in the midst of a local or national disaster that makes clarity, brevity, completeness, and flexibility (backups) key to success. The following are some of the recommended elements in a COOP document:
1. COOP Activation. Conditions for Activating the COOP.
2. COOP Roles and Responsibilities. A matrix of the roles and responsibilities (by position) of all personnel throughout the enterprise who are involved in activating the COOP. Alternates are provided for each position.
3. COOP Checklist. A step-by-step checklist of actions for each person participating in the COOP.
4. COOP Relocation Site Map and Directions. How to get to the COOP site from various probable routes.
5. COOP Relocation Site Activation. The process for activating the COOP site, establishing internal/external communications, and reconstituting key enterprise functions at the COOP site.
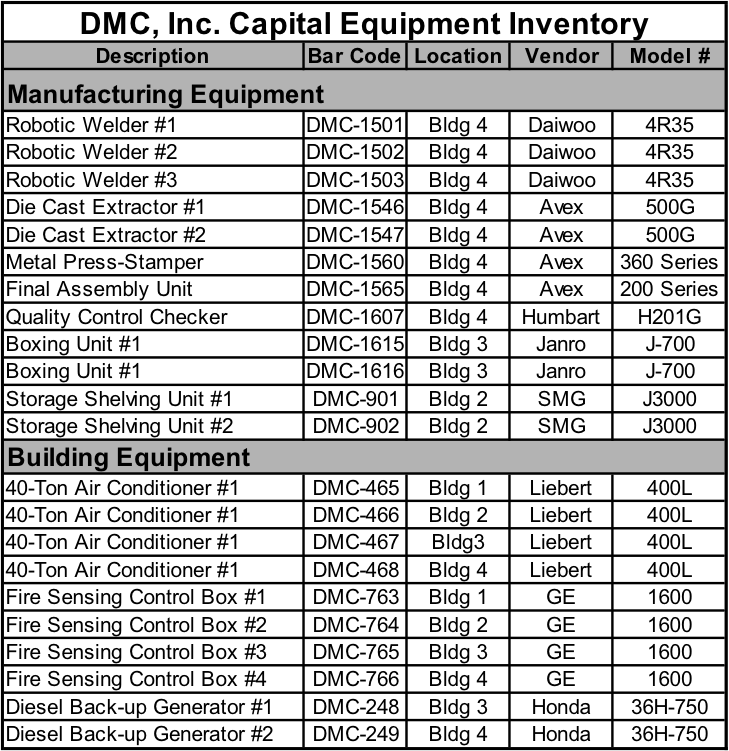
6. COOP Relocation Site Inventory. An inventory of systems, equipment, and supplies at the COOP relocation site, along with the person(s) responsible for ensuring that the systems are operational and the equipment is present when needed.
7. COOP Relocation Site De-Activation. Procedures for de-activating the COOP site and restoring it to a ‘ready status’ after a real relocation event or training exercise.
Enterprise Functions Have to Relocate